CTF UniKL 2018 Writeup: Is it the same?
Written by imrankhairuddin on 7 May 2018
Category : Cryptography
Title : Is it the same?
Points : 100
Attachment: tw3_uni.exe.jpg.pdf.png.apk
Hello there! In this challenge, we are given a unique type of file ‘tw3_uni.exe.jpg.pdf.png.apk’, that seemingly contains no hidden information on first sight.
We tried issuing a ‘file’ command:
root@MLAUPG1: file tw3_uni.exe.jpg.pdf.png.apk
tw3_uni.exe.jpg.pdf.png.apk: JPEG image data, JFIF standard 1.01, resolution (DPI), density 72x72, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=12, height=900, bps=0, PhotometricIntepretation=RGB, orientation=upper-left, width=945] It was an image type file. Then we tried issuing a ‘strings’ command and saw this:

Interesting! At the end of the strings content a url link. Time to go online and look at link .
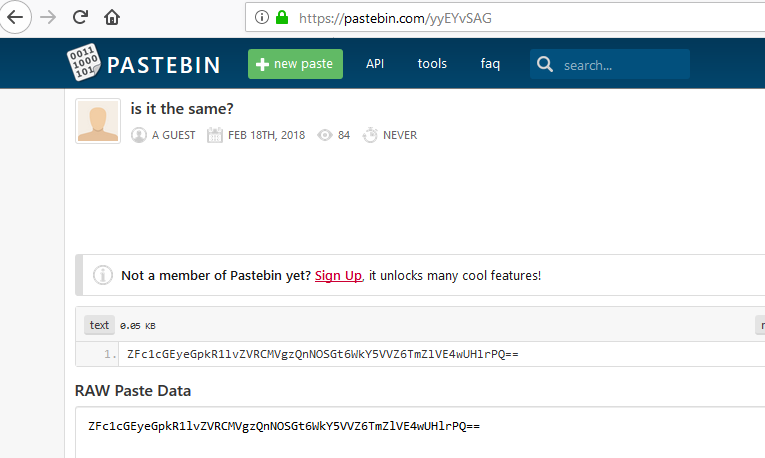
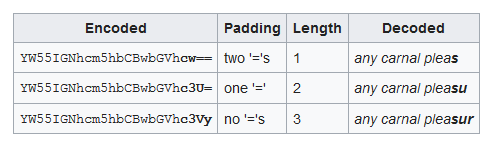
We are getting close. Now we just need to decode the strings with link . When decoding Base64 text, four characters are typically converted back to three bytes. The only exceptions are when padding characters exist. A single ‘=’ indicates that the four characters will decode to only two bytes, while ‘==’ indicates that the four characters will decode to only a single byte. For example:
So, we need to decode it twice. Viola, we got the flag!
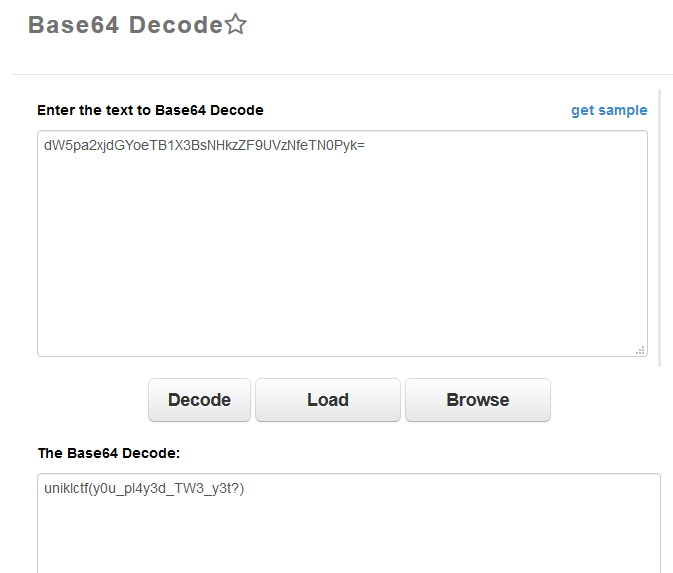
The flag is ‘uniklctf(y0u_pl4y3d_TW3_y3t?)’

